CHAPTER NO. 1: GENESIS OF THE MARKET
1.1 Market Prelude – Introduction & Scope
1.2 The Big Picture – Objectives & Vision
1.3 Strategic Edge – Unique Value Proposition
1.4 Stakeholder Compass – Key Beneficiaries
CHAPTER NO. 2: EXECUTIVE LENS
2.1 Pulse of the Industry – Market Snapshot
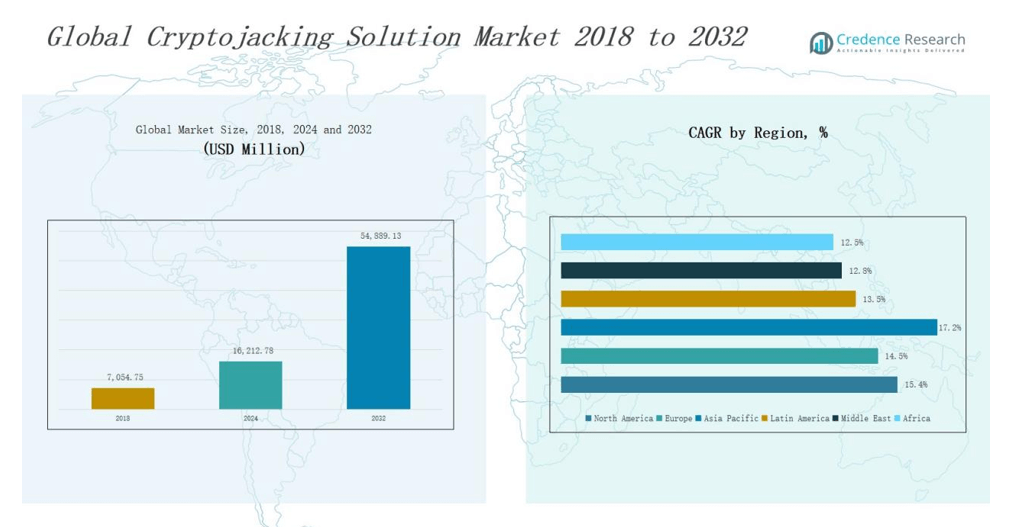
2.2 Growth Arc – Revenue Projections (USD Million)
2.3. Premium Insights – Based on Primary Interviews
CHAPTER NO. 3: CRYPTOJACKING SOLUTION MARKET FORCES & INDUSTRY PULSE
3.1 Foundations of Change – Market Overview
3.2 Catalysts of Expansion – Key Market Drivers
3.2.1 Momentum Boosters – Growth Triggers
3.2.2 Innovation Fuel – Disruptive Technologies
3.3 Headwinds & Crosswinds – Market Restraints
3.3.1 Regulatory Tides – Compliance Challenges
3.3.2 Economic Frictions – Inflationary Pressures
3.4 Untapped Horizons – Growth Potential & Opportunities
3.5 Strategic Navigation – Industry Frameworks
3.5.1 Market Equilibrium – Porter’s Five Forces
3.5.2 Ecosystem Dynamics – Value Chain Analysis
3.5.3 Macro Forces – PESTEL Breakdown
3.6 Price Trend Analysis
3.6.1 Regional Price Trend
3.6.2 Price Trend by Service
CHAPTER NO. 4: KEY INVESTMENT EPICENTER
4.1 Regional Goldmines – High-Growth Geographies
4.2 Service Frontiers – Lucrative Service Categories
4.3 Application Sweet Spots – Emerging Demand Segments
CHAPTER NO. 5: REVENUE TRAJECTORY & WEALTH MAPPING
5.1 Momentum Metrics – Forecast & Growth Curves
5.2 Regional Revenue Footprint – Market Share Insights
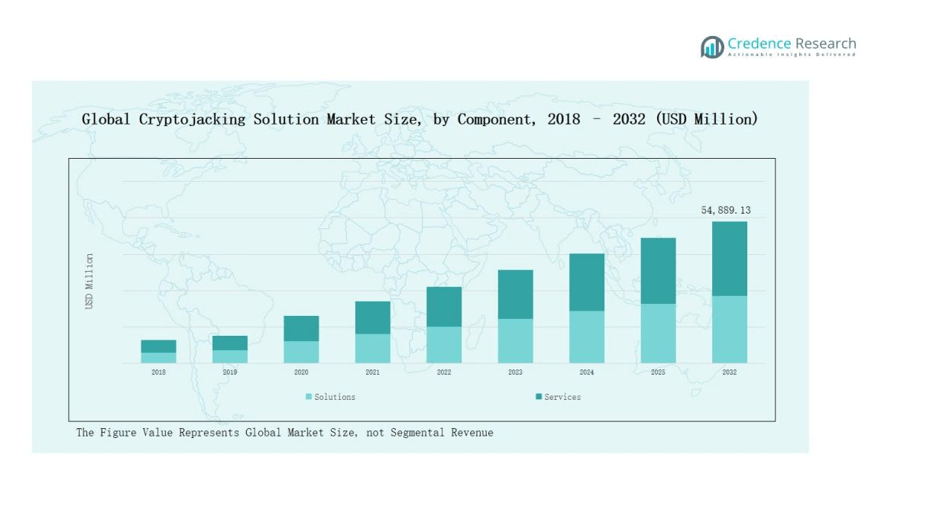
5.3 Segmental Wealth Flow – Component & Deployment Mode Revenue
CHAPTER NO. 6: TRADE & COMMERCE ANALYSIS
6.1. Import Analysis by Region
6.1.1. Global Cryptojacking Solution Market Import Revenue By Region
6.2. Export Analysis by Region
6.2.1. Global Cryptojacking Solution Market Export Revenue By Region
CHAPTER NO. 7: COMPETITION ANALYSIS
7.1. Company Market Share Analysis
7.1.1. Global Cryptojacking Solution Market: Company Market Share
7.2. Global Cryptojacking Solution Market Company Revenue Market Share
7.3. Strategic Developments
7.3.1. Acquisitions & Mergers
7.3.2. New Service Launch
7.3.3. Regional Expansion
7.4. Competitive Dashboard
7.5. Company Assessment Metrics, 2024
CHAPTER NO. 8: CRYPTOJACKING SOLUTION MARKET – BY COMPONENT SEGMENT ANALYSIS
8.1. Cryptojacking Solution Market Overview by Component Segment
8.1.1. Cryptojacking Solution Market Revenue Share By Component
8.2. Solutions
8.3. Services
CHAPTER NO. 9: CRYPTOJACKING SOLUTION MARKET – BY ENTERPRISE SIZE SEGMENT ANALYSIS
9.1. Cryptojacking Solution Market Overview by Enterprise Size Segment
9.1.1. Cryptojacking Solution Market Revenue Share By Enterprise Size
9.2. Small and Medium Enterprises (SMEs)
9.3. Large Enterprises
CHAPTER NO. 10: CRYPTOJACKING SOLUTION MARKET – BY DEPLOYMENT MODE SEGMENT ANALYSIS
10.1. Cryptojacking Solution Market Overview by Deployment Mode Segment
10.1.1. Cryptojacking Solution Market Revenue Share By Deployment Mode
10.2. Cloud-based
10.3. On-premises
CHAPTER NO. 11: CRYPTOJACKING SOLUTION MARKET – BY INDUSTRY VERTICAL SEGMENT ANALYSIS
11.1. Cryptojacking Solution Market Overview by Industry Vertical Segment
11.1.1. Cryptojacking Solution Market Revenue Share By Industry Vertical
11.2. Banking, Financial Services and Insurance (BFSI)
11.3. IT and Telecom
11.4. Healthcare
11.5. Government and Defense
11.6. Others
CHAPTER NO. 12: CRYPTOJACKING SOLUTION MARKET – REGIONAL ANALYSIS
12.1. Cryptojacking Solution Market Overview by Region Segment
12.1.1. Global Cryptojacking Solution Market Revenue Share By Region
12.1.2. Region
12.1.3. Global Cryptojacking Solution Market Revenue By Region
12.1.4. Component
12.1.5. Global Cryptojacking Solution Market Revenue By Component
12.1.6. Enterprise Size
12.1.7. Global Cryptojacking Solution Market Revenue By Enterprise Size
12.1.8. Deployment Mode
12.1.9. Global Cryptojacking Solution Market Revenue By Deployment Mode
12.1.10. Industry Vertical
12.1.11. Global Cryptojacking Solution Market Revenue By Industry Vertical
CHAPTER NO. 13: NORTH AMERICA CRYPTOJACKING SOLUTION MARKET – COUNTRY ANALYSIS
13.1. North America Cryptojacking Solution Market Overview by Country Segment
13.1.1. North America Cryptojacking Solution Market Revenue Share By Region
13.2. North America
13.2.1. North America Cryptojacking Solution Market Revenue By Country
13.2.2. Component
13.2.3. North America Cryptojacking Solution Market Revenue By Component
13.2.4. Enterprise Size
13.2.5. North America Cryptojacking Solution Market Revenue By Enterprise Size
13.2.6. Deployment Mode
13.2.7. North America Cryptojacking Solution Market Revenue By Deployment Mode
13.2.8. Industry Vertical
13.2.9. North America Cryptojacking Solution Market Revenue By Industry Vertical
13.3. U.S.
13.4. Canada
13.5. Mexico
CHAPTER NO. 14: EUROPE CRYPTOJACKING SOLUTION MARKET – COUNTRY ANALYSIS
14.1. Europe Cryptojacking Solution Market Overview by Country Segment
14.1.1. Europe Cryptojacking Solution Market Revenue Share By Region
14.2. Europe
14.2.1. Europe Cryptojacking Solution Market Revenue By Country
14.2.2. Component
14.2.3. Europe Cryptojacking Solution Market Revenue By Component
14.2.4. Enterprise Size
14.2.5. Europe Cryptojacking Solution Market Revenue By Enterprise Size
14.2.6. Deployment Mode
14.2.7. Europe Cryptojacking Solution Market Revenue By Deployment Mode
14.2.8. Industry Vertical
14.2.9. Europe Cryptojacking Solution Market Revenue By Industry Vertical
14.3. UK
14.4. France
14.5. Germany
14.6. Italy
14.7. Spain
14.8. Russia
14.9. Rest of Europe
CHAPTER NO. 15: ASIA PACIFIC CRYPTOJACKING SOLUTION MARKET – COUNTRY ANALYSIS
15.1. Asia Pacific Cryptojacking Solution Market Overview by Country Segment
15.1.1. Asia Pacific Cryptojacking Solution Market Revenue Share By Region
15.2. Asia Pacific
15.2.1. Asia Pacific Cryptojacking Solution Market Revenue By Country
15.2.2. Component
15.2.3. Asia Pacific Cryptojacking Solution Market Revenue By Component
15.2.4. Enterprise Size
15.2.5. Asia Pacific Cryptojacking Solution Market Revenue By Enterprise Size
15.2.6. Deployment Mode
15.2.7. Asia Pacific Cryptojacking Solution Market Revenue By Deployment Mode
15.2.8. Industry Vertical
15.2.9. Asia Pacific Cryptojacking Solution Market Revenue By Industry Vertical
15.3. China
15.4. Japan
15.5. South Korea
15.6. India
15.7. Australia
15.8. Southeast Asia
15.9. Rest of Asia Pacific
CHAPTER NO. 16: LATIN AMERICA CRYPTOJACKING SOLUTION MARKET – COUNTRY ANALYSIS
16.1. Latin America Cryptojacking Solution Market Overview by Country Segment
16.1.1. Latin America Cryptojacking Solution Market Revenue Share By Region
16.2. Latin America
16.2.1. Latin America Cryptojacking Solution Market Revenue By Country
16.2.2. Component
16.2.3. Latin America Cryptojacking Solution Market Revenue By Component
16.2.4. Enterprise Size
16.2.5. Latin America Cryptojacking Solution Market Revenue By Enterprise Size
16.2.6. Deployment Mode
16.2.7. Latin America Cryptojacking Solution Market Revenue By Deployment Mode
16.2.8. Industry Vertical
16.2.9. Latin America Cryptojacking Solution Market Revenue By Industry Vertical
16.3. Brazil
16.4. Argentina
16.5. Rest of Latin America
CHAPTER NO. 17: MIDDLE EAST CRYPTOJACKING SOLUTION MARKET – COUNTRY ANALYSIS
17.1. Middle East Cryptojacking Solution Market Overview by Country Segment
17.1.1. Middle East Cryptojacking Solution Market Revenue Share By Region
17.2. Middle East
17.2.1. Middle East Cryptojacking Solution Market Revenue By Country
17.2.2. Component
17.2.3. Middle East Cryptojacking Solution Market Revenue By Component
17.2.4. Enterprise Size
17.2.5. Middle East Cryptojacking Solution Market Revenue By Enterprise Size
17.2.6. Deployment Mode
17.2.7. Middle East Cryptojacking Solution Market Revenue By Deployment Mode
17.2.8. Industry Vertical
17.2.9. Middle East Cryptojacking Solution Market Revenue By Industry Vertical
17.3. GCC Countries
17.4. Israel
17.5. Turkey
17.6. Rest of Middle East
CHAPTER NO. 18: AFRICA CRYPTOJACKING SOLUTION MARKET – COUNTRY ANALYSIS
18.1. Africa Cryptojacking Solution Market Overview by Country Segment
18.1.1. Africa Cryptojacking Solution Market Revenue Share By Region
18.2. Africa
18.2.1. Africa Cryptojacking Solution Market Revenue By Country
18.2.2. Component
18.2.3. Africa Cryptojacking Solution Market Revenue By Component
18.2.4. Enterprise Size
18.2.5. Africa Cryptojacking Solution Market Revenue By Enterprise Size
18.2.6. Deployment Mode
18.2.7. Africa Cryptojacking Solution Market Revenue By Deployment Mode
18.2.8. Industry Vertical
18.2.9. Africa Cryptojacking Solution Market Revenue By Industry Vertical
18.3. South Africa
18.4. Egypt
18.5. Rest of Africa
CHAPTER NO. 19: COMPANY PROFILES
19.1. Cisco Systems, Inc.
19.1.1. Company Overview
19.1.2. Service Portfolio
19.1.3. Financial Overview
19.1.4. Recent Developments
19.1.5. Growth Strategy
19.1.6. SWOT Analysis
19.2. Palo Alto Networks
19.3. McAfee LLC
19.4. Symantec Corporation
19.5. CrowdStrike Holdings, Inc.
19.6. Check Point Software Technologies Ltd.
19.7. Trend Micro Incorporated
19.8. Sophos Group plc
19.9. Kaspersky Lab
19.10. FireEye, Inc.