Market Overview
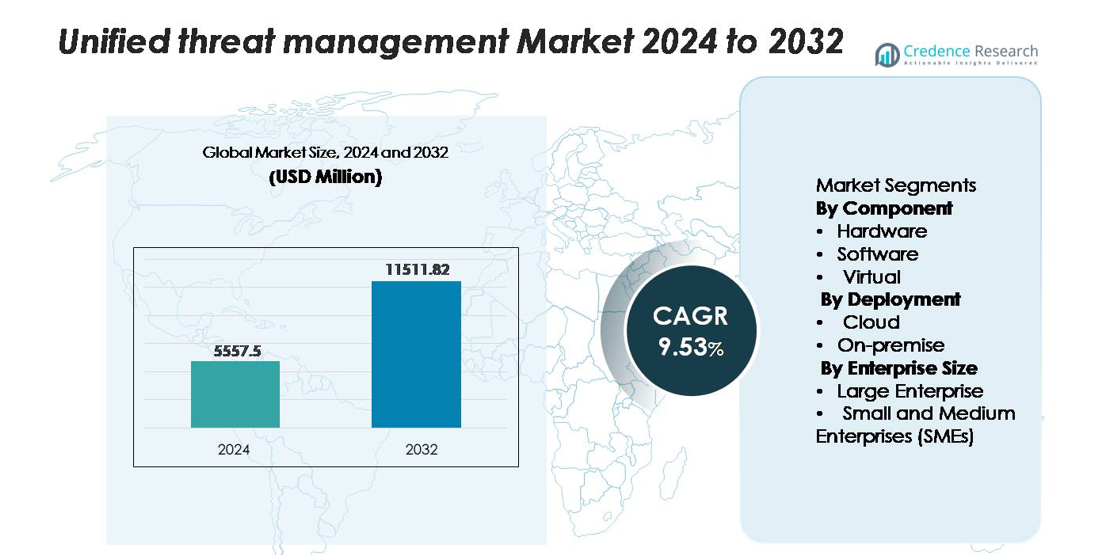
The global Unified Threat Management (UTM) market was valued at USD 5,557.5 million in 2024 and is projected to reach USD 11,511.82 million by 2032, expanding at a CAGR of 9.53% during the forecast period.
| REPORT ATTRIBUTE |
DETAILS |
| Historical Period |
2020-2023 |
| Base Year |
2024 |
| Forecast Period |
2025-2032 |
| Unified Threat Management Market Size 2024 |
USD 5,557.5 million |
| Unified Threat Management Market, CAGR |
9.53% |
| Unified Threat Management Market Size 2032 |
USD 11,511.82 million |
Leading vendors in the Unified Threat Management (UTM) market include Fortinet, Cisco Systems, Sophos, Check Point Software Technologies, and WatchGuard Technologies, all of which offer integrated platforms combining firewalling, intrusion prevention, secure VPN, web filtering, and centralized policy control. These players strengthen competitiveness through high-performance appliances, cloud-delivered security models, and AI-enhanced threat intelligence. North America represents the largest regional market with approximately 40.5% share, driven by advanced cybersecurity maturity, extensive cloud adoption, and strong enterprise spending. Europe, with nearly 30% share, remains the second-largest region, supported by strict compliance mandates and expanding digital-infrastructure protection needs.
Market Insights
- The Unified Threat Management (UTM) market was valued at USD 5,557.5 million in 2024 and is projected to reach USD 11,511.82 million by 2032, registering a CAGR of 9.53% during the forecast period.
- Market growth is driven by rising multi-vector cyberattacks, expanding hybrid networks, and increasing enterprise need for consolidated security platforms integrating firewall, IPS, VPN, and threat-intelligence features across a single interface.
- Key trends include rapid adoption of cloud-delivered UTMs, integration of AI-driven threat analytics, and growing demand for virtual appliances supporting virtualized and multi-cloud workloads; hardware remains the dominant component segment.
- The competitive landscape is shaped by leading players such as Fortinet, Cisco, Sophos, Check Point, and WatchGuard, each enhancing performance, scalability, and unified management capabilities; restraints include performance bottlenecks and rising configuration complexity.
- Regionally, North America holds ~40.5% share, followed by Europe at ~30% and Asia-Pacific with 20–35%; by deployment, cloud-based UTMs lead due to scalability and centralized visibility.
Access crucial information at unmatched prices!
Request your sample report today & start making informed decisions powered by Credence Research Inc.!
Download Sample
Market Segmentation Analysis:
By Component
Hardware remains the dominant component segment, capturing the largest market share as enterprises continue to rely on dedicated UTM appliances for high-performance perimeter protection, integrated routing, and consolidated threat detection. Demand is reinforced by organizations seeking unified firewall, intrusion prevention, VPN, and gateway filtering in a single on-site device to streamline management and reduce complexity. Software-based UTMs are gaining traction as businesses adopt flexible licensing models and enhanced analytics features, while virtual UTMs expand steadily due to virtualization adoption and the need for scalable, hypervisor-based security enforcement across distributed environments.
- For instance, Fortinet’s FortiGate 1800F—a widely deployed hardware UTM appliance—delivers 198 Gbps firewall throughput and 20 Gbps threat protection performance, providing enterprises with high-capacity inspection required for hardware-led UTM deployments.
By Deployment
Cloud deployment holds the dominant market share, driven by rapid migration to hybrid and multi-cloud infrastructures requiring centralized, elastic, and continuously updated security controls. Organizations prefer cloud-delivered UTMs for their faster provisioning, subscription flexibility, and reduced hardware overhead. This model also enables real-time threat intelligence updates and improved protection against emerging attacks. On-premise deployment remains relevant for sectors with strict data residency and compliance mandates, offering full operational control and low-latency processing for sensitive workloads, particularly in regulated industries and geographically isolated environments.
- For instance, Sophos Firewall’s virtual XGS series can be deployed across various cloud environments, including VMware, Hyper-V, and KVM. These virtual appliances scale up to 16 cores in standard licensed configurations, with an “unlimited core” license option available.
By Enterprise Size
Large enterprises dominate the market share due to their extensive IT ecosystems, higher exposure to complex cyber threats, and increased adoption of integrated security architectures requiring advanced UTM solutions. They invest in multi-layered inspection, high-throughput appliances, and unified policy management to secure numerous branch offices and cloud-connected assets. Small and Medium Enterprises (SMEs) demonstrate strong growth momentum as they prioritize cost-effective, all-in-one security platforms to simplify protection and reduce administrative burden. Subscription-based models and managed UTM services further accelerate adoption among resource-constrained SME environments.
Key Growth Drivers
Rising Complexity of Cyber Threats and Expanding Attack Surface
The accelerating volume and sophistication of cyberattacks continue to fuel demand for Unified Threat Management solutions. Enterprises face evolving threats such as multi-vector intrusions, ransomware-as-a-service, encrypted malware, and advanced phishing campaigns that bypass traditional security tools. As organizations expand their digital ecosystems through mobile endpoints, hybrid cloud adoption, and distributed workforces, the attack surface grows significantly. UTM platforms provide consolidated defenses integrating firewalling, intrusion prevention, antivirus, gateway filtering, and secure VPN capabilities, allowing enterprises to combat diverse threats through a single management console. This convergence reduces operational fragmentation and ensures consistent policy enforcement across networks. Growing regulatory pressure around data protection, incident reporting, and cybersecurity compliance further encourages enterprises to adopt comprehensive, unified frameworks capable of real-time threat detection and rapid response orchestration.
- For instance, Check Point’s Quantum 6600 appliance delivers 18 Gbps of firewall throughput and 3.7 Gbps threat prevention performance (under enterprise testing conditions), enabling organizations to inspect large encrypted traffic volumes while maintaining advanced threat visibility across expanding attack surfaces.
Growing Demand for Cost-Efficient & Integrated Security Solutions
Budget-conscious organizations, particularly SMEs, increasingly adopt UTM platforms to reduce the complexity and cost associated with managing multiple standalone security products. A single UTM appliance eliminates the need to license, deploy, integrate, and maintain separate intrusion prevention systems, web filters, VPN gateways, and anti-malware engines. This consolidation not only lowers upfront expenditures but also reduces hidden operational costs linked to maintenance, vendor coordination, and specialized security talent. As IT teams face capacity constraints, the simplified architecture of UTM solutions enables easier administration, automated updates, and centralized policy management. Cloud-based UTMs further increase affordability by offering consumption-based pricing and flexible scalability. The shift toward integrated protection is also driven by growing awareness of security gaps that arise when fragmented tools fail to exchange intelligence or provide unified visibility.
- For instance, WatchGuard’s Firebox T85 delivers up to 4.96 Gbps firewall throughput and over 940 Mbps threat protection performance (UTM full scan) within a compact desktop form factor, giving SMEs enterprise-grade inspection capacity without requiring multiple security appliances.
Rapid Growth of Remote Work and Distributed Network Architectures
The global shift toward remote and hybrid work environments has intensified the need for unified security approaches protecting users, devices, and corporate networks irrespective of location. UTM solutions support secure VPN deployments, encrypted tunnels, identity-based access, and continuous traffic inspection—capabilities essential for safeguarding employees working across unsecured home networks and public Wi-Fi environments. As enterprises expand digital operations across branch offices and distributed edge locations, UTM devices enable scalable perimeter protection with consistent security policies. The integration of SD-WAN functionalities in modern UTM platforms further enhances performance by optimizing traffic routing while maintaining threat inspection across dispersed networks. Remote work has also increased cloud service adoption, reinforcing the need for UTMs with cloud security gateways and unified analytics to maintain end-to-end visibility and control across hybrid environments.
Key Trends & Opportunities
Expansion of Cloud-Delivered UTM and Security-as-a-Service Models
Cloud-based UTM deployment continues to accelerate as enterprises transition toward cloud-first strategies and decentralized IT environments. Cloud-delivered UTM solutions offer elastic scaling, automated updates, and real-time global threat intelligence, addressing limitations of hardware-bound appliances. This trend creates opportunities for vendors to offer Security-as-a-Service (SECaaS) models that simplify implementation and reduce capital expenditures. Organizations benefit from centralized dashboards that manage virtual firewalls, sandboxing, access controls, and intrusion prevention across multiple cloud platforms. The ongoing shift toward containerized applications and serverless computing further increases the relevance of cloud-native UTM capabilities. Vendors can tap into rising demand for secure cloud gateways and multi-tenant architectures tailored for managed service providers that serve large SME bases. As enterprises adopt hybrid and multi-cloud networks, cloud-delivered UTM emerges as a critical growth avenue.
- For instance, Cisco’s Secure Firewall Threat Defense Virtual (FTDv) supports up to 16 vCPUs and delivers 14 Gbps firewall throughput in cloud-optimized configurations, enabling high-capacity inspection across hybrid and multi-cloud environments.
Integration of AI, Behavioral Analytics, and Zero-Trust Capabilities
A major trend shaping the UTM market is the integration of artificial intelligence, machine learning, and behavioral analytics to enhance real-time threat detection and reduce reliance on manual security operations. AI-enabled UTMs can analyze traffic patterns, user behavior, and anomaly signals to identify previously unknown threats, automate incident response actions, and improve overall detection accuracy. Vendors are embedding zero-trust network access (ZTNA) principles—such as continuous verification, micro-segmentation, and identity-based policies—into UTM frameworks to address modern attack vectors that exploit lateral movement. This integration unlocks opportunities for delivering more advanced, predictive, and context-aware security. Enterprises increasingly seek such intelligent capabilities to counter sophisticated attacks, reduce false positives, and maintain security across dynamic environments involving remote workforces, IoT devices, and virtualized networks.
- For instance, Trend Micro’s Vision One platform processes over 6 trillion security events per year and integrates telemetry from 35+ native and third-party sensors, enabling AI-driven correlation that feeds directly into Zero-Trust policy engines for dynamic and automated threat containment.
Growing Adoption of Virtual UTMs for Hybrid and Virtualized Environments
The rise of virtualization, hyperconverged infrastructures, and software-defined networking is creating strong opportunities for virtualized UTM deployments. Virtual UTMs allow enterprises to implement security directly within hypervisors, cloud workloads, and virtual private clouds without relying on physical appliances. They provide rapid provisioning, lower deployment costs, and scalability aligned with virtual machine growth. As businesses expand hybrid-cloud operations, virtual UTMs ensure consistent protection across multi-location environments while supporting containerized workloads and microservices architectures. This trend is particularly strong among large enterprises that require flexible, scalable, and automation-friendly security models. Vendors offering virtual form factors with high throughput, API integrations, and orchestration compatibility are well-positioned to capture the rising demand from digitally mature organizations.
Key Challenges
Performance Bottlenecks and Scalability Limitations in High-Traffic Environments
One of the most significant challenges faced by UTM systems is the potential for performance degradation when multiple security functions operate simultaneously, especially in high-bandwidth or latency-sensitive environments. As network traffic grows due to cloud adoption, IoT device proliferation, and high-volume encrypted data flows, UTM appliances may struggle to maintain throughput while performing deep packet inspection, SSL decryption, intrusion prevention, and malware scanning concurrently. Organizations with large distributed infrastructures often require advanced, high-capacity appliances, increasing deployment and upgrade costs. Performance limitations pose risks when enterprises rely heavily on real-time threat detection and continuous inspection. Vendors must enhance hardware acceleration, optimize software engines, and adopt intelligent inspection techniques to overcome these scalability concerns.
Skills Shortage and Complexity in Managing Evolving Threat Ecosystems
Despite their integrated nature, UTM platforms still require skilled professionals who understand complex threat landscapes, policy configurations, and multi-layered security functions. The global cybersecurity talent shortage makes it difficult for enterprises—especially SMEs—to deploy, fine-tune, and maintain UTM systems effectively. Misconfigurations, improper rule updates, and lack of continuous monitoring can create vulnerabilities that attackers may exploit. As threats evolve rapidly, enterprises must consistently adapt policies and maintain threat intelligence feeds, placing operational strain on limited security teams. The complexity increases further in hybrid infrastructures where UTMs must interact with cloud-native tools, identity systems, and endpoint detection platforms. Addressing this challenge requires vendor investments in automation, simplified interfaces, and managed UTM service offerings.
Regional Analysis
North America
North America dominates the UTM market with roughly 40.5% market share, driven by the U.S. and Canada’s advanced IT infrastructure, high cybersecurity awareness, and extensive cloud adoption. Enterprises across this region face sophisticated threat landscapes and regulatory pressures, prompting consolidated security investments. The presence of mature managed security service providers (MSSPs) and leading UTM vendors strengthens market penetration. Organizations prefer unified platforms that combine firewall, intrusion prevention, VPN, and content-filtering capabilities, thereby simplifying management and reducing overhead in large distributed networks.
Europe
Europe accounts for approximately 30% of the global UTM market, underpinned by stringent data-privacy regulations (e.g., GDPR) and a diverse industrial base spanning manufacturing, finance, healthcare and telecom. Enterprises in the UK, Germany, France and Nordics increasingly deploy unified threat management solutions to address regulatory compliance, protect critical infrastructure and manage multi-country operations. Growth is further propelled by rising cyber-attack rates, digital transformation across EU economies, and the necessity of integrated security frameworks that offer centralized visibility and administration across complex network architectures.
Asia-Pacific
The Asia-Pacific region holds an estimated 20 %–35% market share and is the fastest-growing region for UTM adoption. Countries such as China, India, Japan and Southeast Asia are experiencing rapid digitalisation, cloud migration and increasing cybersecurity investment from both enterprises and governments. SMEs in the region favour cost-effective, all-in-one UTM platforms to secure remote branches, distributed operations and mobile workforces. Vendor expansion, building of local channel ecosystems and strengthening of regional cloud-security frameworks further accelerate uptake of UTM solutions across diverse verticals.
Latin America
Latin America constitutes around 5 %–8% of the global UTM market. Growth is led by Brazil, Mexico and Chile, where enterprises and public-sector organisations are modernising security postures in response to rising ransomware incidences and digital-service adoption. UTM solutions appeal due to their consolidated functionality, affordability and simplified management, especially for mid-sized organisations. The region’s increasing cloud migration, demand for localised security services and expanding MSSP presence further enhance market momentum notwithstanding economic and infrastructure-related constraints.
Middle East & Africa
The Middle East & Africa (MEA) region holds an approximate 4 %–6% share of the global UTM market. The growth is driven by national digital-transformation initiatives, smart infrastructure deployments and increasing cybersecurity spend in Gulf Cooperation Council (GCC) countries, South Africa and Nigeria. Organisations deploy UTM solutions to safeguard branch networks, remote operations and cloud-connected assets, often underpinned by government cybersecurity mandates. The limited pool of skilled security professionals and the fragmented security frameworks in emerging markets amplify demand for integrated UTM platforms and managed-service offerings.
Market Segmentations:
By Component
- Hardware
- Software
- Virtual
By Deployment
By Enterprise Size
- Large Enterprise
- Small and Medium Enterprises (SMEs)
By Geography
- North America
- Europe
- Germany
- France
- U.K.
- Italy
- Spain
- Rest of Europe
- Asia Pacific
- China
- Japan
- India
- South Korea
- South-east Asia
- Rest of Asia Pacific
- Latin America
- Brazil
- Argentina
- Rest of Latin America
- Middle East & Africa
- GCC Countries
- South Africa
- Rest of the Middle East and Africa
Competitive Landscape
The competitive landscape of the Unified Threat Management (UTM) market is characterized by strong participation from global cybersecurity leaders offering integrated, high-performance security platforms. Companies such as Fortinet, Cisco Systems, Sophos, Check Point Software Technologies, and WatchGuard Technologies dominate through extensive product portfolios that combine firewalling, intrusion prevention, secure VPN, web filtering, and centralized policy management. These vendors emphasize high throughput, low-latency inspection, and AI-enhanced threat detection to meet the needs of hybrid and distributed networks. Competitive differentiation increasingly depends on cloud-delivered UTM services, virtual appliance scalability, automated updates, and unified management consoles designed to reduce operational complexity. Emerging players strengthen their presence through managed security service partnerships and modular subscription models targeting SMEs. As cyber threats grow more sophisticated and enterprise networks expand across multi-cloud environments, vendors continue investing in advanced analytics, zero-trust capabilities, and simplified orchestration to maintain market leadership and capture evolving customer requirements.
Shape Your Report to Specific Countries or Regions & Enjoy 30% Off!
Key Player Analysis
- Fortinet, Inc.
- Sophos Ltd.
- Cisco Systems, Inc.
- WatchGuard Technologies, Inc.
- Juniper Networks, Inc.
- Huawei Technologies Co., Ltd.
- Check Point Software Technologies Ltd.
- Trend Micro Incorporated
- SonicGuard
- Untangle
Recent Developments
- In November 2025, Cisco issued a security advisory disclosing active exploitation of its Secure Firewall ASA/FTD devices via vulnerabilities CVE-2025-20333 and CVE-2025-20362.
- In January 2025, Juniper announced the latest evolution of its “Juniper Partner Advantage” programme (Jan 2025) to enhance partner resources, support and profitability—though the update is more channel-focused than specific to UTM appliance launches.
- In February 2025, Check Point announced six new AI-powered innovations for its Infinity Platform to accelerate zero-trust, strengthen threat prevention, and simplify security operations
Report Coverage
The research report offers an in-depth analysis based on Component, Deployment, Enterprise size and Geography. It details leading market players, providing an overview of their business, product offerings, investments, revenue streams, and key applications. Additionally, the report includes insights into the competitive environment, SWOT analysis, current market trends, as well as the primary drivers and constraints. Furthermore, it discusses various factors that have driven market expansion in recent years. The report also explores market dynamics, regulatory scenarios, and technological advancements that are shaping the industry. It assesses the impact of external factors and global economic changes on market growth. Lastly, it provides strategic recommendations for new entrants and established companies to navigate the complexities of the market.
Future Outlook
- UTM platforms will increasingly integrate AI-driven threat detection to improve real-time response and reduce false positives.
- Cloud-delivered UTM services will expand as enterprises accelerate hybrid and multi-cloud adoption.
- Virtual UTMs will grow rapidly to support virtualized workloads, container environments, and software-defined architectures.
- UTM vendors will strengthen zero-trust capabilities to secure distributed networks and remote workforces.
- Consolidation of security functions will intensify as organizations seek simplified management and unified policy control.
- High-performance UTM appliances will evolve to handle rising encrypted traffic and advanced inspection workloads.
- Managed security service providers will play a larger role in delivering UTM solutions to SMEs.
- Integration with SD-WAN will deepen, enabling secure and optimized branch-network connectivity.
- Regulatory compliance requirements will continue driving adoption across regulated sectors.
- Global demand will rise as cyber threats intensify and organizations prioritize unified, scalable security frameworks.




