Market Overview
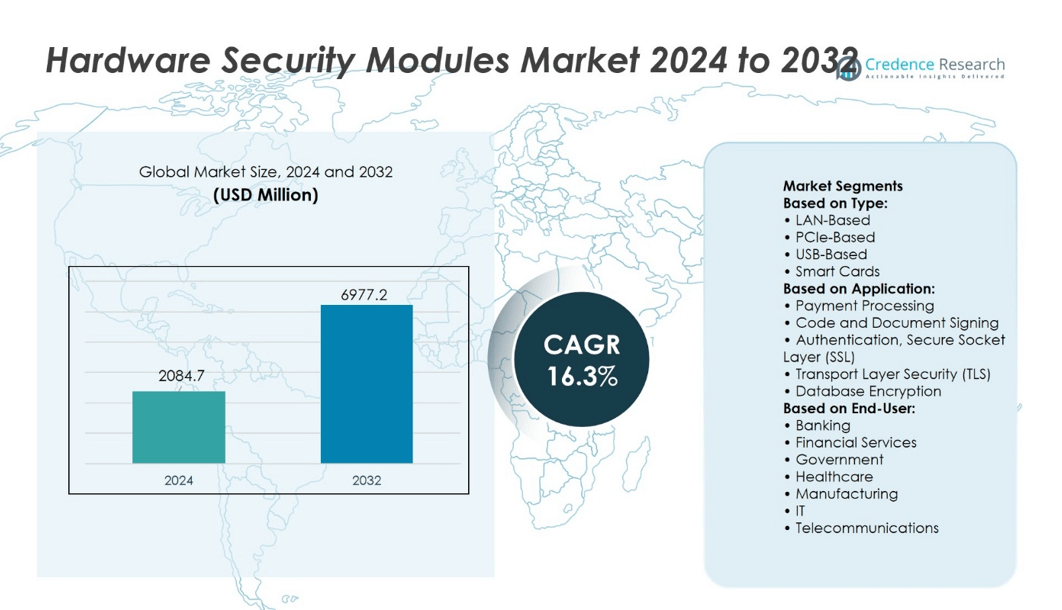
Hardware Security Modules Market size was valued at USD 2084.7 million in 2024 and is anticipated to reach USD 6977.2 million by 2032, at a CAGR of 16.3% during the forecast period.
| REPORT ATTRIBUTE |
DETAILS |
| Historical Period |
2020-2023 |
| Base Year |
2024 |
| Forecast Period |
2025-2032 |
| Hardware Security Modules Market Size 2024 |
USD 2084.7 million |
| Hardware Security Modules Market, CAGR |
16.3% |
| Hardware Security Modules Market Size 2032 |
USD 6977.2 million |
The Hardware Security Modules Market grows through rising demand for secure cryptographic key management across banking, government, healthcare, and cloud services. It benefits from stricter regulatory compliance mandates, increasing reliance on digital payment systems, and expanding adoption in hybrid and multi-cloud environments. Key trends include integration with post-quantum cryptography, deployment in IoT and edge applications, and growth of service-based delivery models. Vendors focus on enhancing interoperability, scalability, and energy efficiency while supporting emerging use cases in blockchain and 5G networks. Continuous innovation and alignment with evolving security standards strengthen its role in safeguarding critical data and infrastructure.
The Hardware Security Modules Market shows strong presence in North America, Europe, and Asia-Pacific, with growing adoption in Latin America and the Middle East & Africa. North America leads due to advanced cybersecurity infrastructure, while Europe benefits from strict data protection laws, and Asia-Pacific experiences rapid growth from digital payment expansion. Key players include Thales Group, International Business Machines Corporation, Hewlett Packard Enterprise Development LP, Atos SE, Utimaco GmbH, Futurex, Securosys SA, Entrust Corporation, Exceet Secure Solutions GmbH, and Yubico AB.
Market Insights
- The Hardware Security Modules Market was valued at USD 2084.7 million in 2024 and is projected to reach USD 6977.2 million by 2032, at a CAGR of 16.3%.
- Rising demand for secure cryptographic key management in banking, government, healthcare, and cloud services drives market growth.
- Key trends include integration with post-quantum cryptography, expansion into IoT and edge applications, and increasing adoption of service-based delivery models.
- Competition is marked by innovation, compliance readiness, and integration with hybrid and multi-cloud infrastructures.
- High implementation costs and deployment complexities act as restraints for small and mid-sized enterprises.
- North America leads due to advanced cybersecurity infrastructure, followed by Europe with strict data protection laws, and Asia-Pacific with rapid digital payment adoption.
- Leading players include Thales Group, International Business Machines Corporation, Hewlett Packard Enterprise Development LP, Atos SE, Utimaco GmbH, Futurex, Securosys SA, Entrust Corporation, Exceet Secure Solutions GmbH, and Yubico AB.
Access crucial information at unmatched prices!
Request your sample report today & start making informed decisions powered by Credence Research Inc.!
Download Sample
Market Drivers
Rising Need for Data Protection in Expanding Digital Ecosystems
The Hardware Security Modules Market benefits from increasing demand for robust data protection across financial services, healthcare, and government sectors. Organizations rely on it to secure cryptographic keys, authenticate transactions, and safeguard sensitive assets from evolving cyber threats. Expanding digital transformation initiatives and regulatory compliance requirements amplify adoption. Enterprises prioritize tamper-resistant hardware over software-based solutions to mitigate risks of key theft or misuse. The capability to support high-volume cryptographic processing while maintaining performance strengthens its value proposition. This security focus aligns with the growing reliance on connected systems and cloud infrastructures.
- For instance, Utimaco Atalla HSMs handled 250 million card transactions each day (over a billion transactions annually).
Stringent Compliance Mandates and Regulatory Frameworks Driving Adoption
Global regulations such as GDPR, PCI DSS, and FIPS 140-3 encourage wider deployment of hardware security modules in regulated industries. The Hardware Security Modules Market sees increased uptake from businesses aiming to achieve and maintain certification under these frameworks. It ensures data integrity, confidentiality, and accountability in both on-premises and hybrid IT environments. Compliance-driven procurement often prioritizes devices with validated security standards and interoperability features. This compliance focus reinforces trust among customers and partners while reducing legal and reputational risks. Rising cross-border data flows further highlight the need for certified encryption solutions.
- For instance, as of its most recent compliance cycle, AWS CloudHSM has processed 2 million cryptographic operations per month under its FIPS 140-3 Level 3 certified service.
Shift Toward Cloud and Hybrid Deployments Enhancing Integration Opportunities
Enterprises migrate workloads to cloud platforms while retaining control over encryption keys, boosting demand for hardware security modules that integrate with multi-cloud environments. The Hardware Security Modules Market responds with scalable, API-enabled solutions compatible with public and private clouds. It supports secure key management for data-at-rest and data-in-transit across geographically distributed infrastructures. Providers offer subscription-based or as-a-service models to address evolving capacity requirements. The ability to deliver centralized policy control while ensuring low-latency cryptographic operations enhances appeal. Cloud adoption trends expand use cases beyond traditional financial and government domains.
Growth in Emerging Use Cases Across IoT, Blockchain, and 5G Applications
Rapid development in IoT ecosystems, blockchain-based services, and 5G networks creates new security challenges that require hardware-grade encryption. The Hardware Security Modules Market addresses these demands with solutions optimized for high-throughput, low-latency operations in distributed architectures. It enables secure identity provisioning, firmware integrity checks, and cryptographic transaction validation at scale. Telecom operators integrate hardware security modules into core networks to safeguard subscriber data and signaling channels. Blockchain platforms deploy them for key custody, transaction signing, and consensus verification. Expanding adoption in these high-growth sectors extends market relevance beyond traditional enterprise IT.
Market Trends
Increasing Integration of Hardware Security Modules in Cloud-Native Architectures
The Hardware Security Modules Market reflects a clear trend toward integration with cloud-native infrastructures. Enterprises seek secure key management that aligns with containerized and microservices-based deployments. It enables cryptographic operations in dynamic environments while preserving compliance with data protection mandates. Vendors develop hardware security modules that support cloud provider key management services and multi-cloud strategies. Hybrid models combine on-premises devices with virtualized instances for operational flexibility. This trend supports organizations aiming to balance scalability, performance, and security across diverse IT ecosystems.
- For instance, Google Cloud’s Cloud HSM for Google Workspace supported 20 million encrypt/decrypt operations in a single billing month in a documented usage example.
Expansion of Hardware Security Modules into Emerging Edge and IoT Applications
Adoption expands into edge computing and IoT deployments where localized security is critical. The Hardware Security Modules Market sees growing demand for compact, energy-efficient devices capable of operating in constrained environments. It secures identity, data transmission, and firmware integrity in connected devices. Manufacturers introduce ruggedized and modular designs to withstand harsh industrial or outdoor conditions. Integration with IoT gateways and edge servers enables decentralized encryption processes without relying solely on centralized infrastructure. This shift addresses the security needs of smart manufacturing, energy distribution, and connected transport systems.
- For instance, Thales reported that its HSM solutions deployed in IoT and edge environments secured over 4.8 million API calls annually for connected devices.
Adoption of Post-Quantum Cryptography Standards in Hardware Security Modules
Industry preparations for quantum-era threats drive the inclusion of post-quantum cryptographic algorithms in hardware security modules. The Hardware Security Modules Market adapts by offering firmware updates and hardware designs ready for quantum-resistant encryption. It supports secure migration paths for enterprises seeking long-term data protection. Collaboration between vendors, standards bodies, and cybersecurity agencies accelerates the adoption of these algorithms. The trend ensures that sensitive data remains secure against potential future decryption capabilities of quantum computers. Early adoption reinforces the market’s role in proactive security innovation.
Rising Demand for Subscription and as-a-Service Deployment Models
Subscription-based and Hardware Security Module-as-a-Service models gain momentum across industries seeking flexible procurement options. The Hardware Security Modules Market benefits from organizations preferring operational expenditure over capital-intensive investments. It allows rapid deployment, predictable cost structures, and scalability based on demand. Service providers bundle hardware with managed cryptographic operations, reducing the need for in-house expertise. This approach appeals to mid-sized enterprises and startups entering regulated markets. The shift supports broader accessibility to high-assurance security solutions without complex infrastructure commitments.
Market Challenges Analysis
High Implementation Costs and Complexity in Deployment Across Diverse Environments
The Hardware Security Modules Market faces the challenge of high upfront costs and operational complexities that limit adoption in smaller enterprises. It requires specialized hardware, integration expertise, and ongoing maintenance that increase total cost of ownership. Organizations with distributed or hybrid infrastructures often encounter difficulties aligning hardware security modules with varied IT frameworks. Compatibility issues with legacy systems and proprietary applications can slow deployment timelines. Limited internal expertise in cryptographic key management further complicates implementation. These factors create barriers for organizations seeking to balance security needs with budget constraints.
Evolving Threat Landscape and Rapid Technological Obsolescence
Constant advancements in cyberattack techniques put pressure on hardware security module vendors to innovate at a rapid pace. The Hardware Security Modules Market must address emerging threats such as side-channel attacks, advanced malware, and future quantum computing risks. It faces the challenge of ensuring long product lifecycles while keeping pace with evolving encryption standards. Frequent firmware and hardware upgrades may disrupt operations for organizations with mission-critical workloads. Vendors also contend with the need for global compliance updates, which can vary by region and industry. The pace of change increases operational and financial demands on both providers and end users.
Market Opportunities
Expansion into High-Growth Sectors Such as IoT, 5G, and Blockchain Applications
The Hardware Security Modules Market holds significant opportunity in sectors requiring secure, high-speed cryptographic operations at scale. It can strengthen IoT ecosystems by safeguarding device identities, securing data exchange, and protecting firmware integrity in connected environments. In 5G networks, hardware security modules support subscriber data protection and secure signaling, enabling telecom operators to meet stringent security standards. Blockchain platforms present further potential, with hardware devices enabling secure key custody, transaction validation, and consensus integrity. Vendors offering compact, energy-efficient, and integration-ready designs can capture share in these emerging fields. The rising adoption of decentralized and high-throughput digital services reinforces this growth avenue.
Growing Demand for Cloud-Integrated and As-a-Service Security Solutions
Enterprises seeking flexibility in security infrastructure create opportunities for cloud-integrated hardware security modules and subscription-based delivery models. The Hardware Security Modules Market benefits from this shift by offering scalable solutions that align with hybrid and multi-cloud strategies. It allows organizations to maintain control over cryptographic keys while leveraging cloud scalability and cost efficiency. Service-based offerings appeal to enterprises without in-house expertise, lowering barriers to adoption in regulated industries. Integration with cloud-native key management services enhances operational agility while ensuring compliance with global data protection mandates. The combination of predictable costs and simplified deployment expands the addressable market for security providers.
Market Segmentation Analysis:
By Type
The Hardware Security Modules Market segments by type into LAN-based, PCIe-based, USB-based, smart cards, and others, each serving distinct operational requirements. LAN-based modules dominate in large enterprises where centralized key management supports multiple applications across secure networks. PCIe-based solutions integrate directly into servers, offering high-speed cryptographic processing for data centers and financial transaction systems. USB-based modules provide portability and ease of use for developers, auditors, and small-scale secure deployments. Smart cards serve identity authentication and secure access control in government and enterprise settings. It maintains diversity in form factors to address both high-throughput and portable security needs across industries.
- For instance, Thales reported that its LAN-based Luna Network HSMs handled over 2,300 million cryptographic transactions annually.
By Application
Application segmentation includes payment processing, code and document signing, authentication, SSL/TLS, database encryption, and other specialized uses. Payment processing remains a core driver, with hardware security modules safeguarding PIN verification, EMV transactions, and financial clearing operations. Code and document signing applications ensure software integrity and compliance in industries such as aerospace, automotive, and pharmaceuticals. Authentication functions secure access to critical systems and resources in corporate and government environments. SSL/TLS applications protect sensitive online transactions and communications, while database encryption safeguards structured data in enterprise systems. It supports mission-critical processes where cryptographic assurance directly impacts regulatory compliance and operational trust.
- For instance, AWS Payment Cryptography processed 15 million card transactions per month in a documented usage scenario, each transaction involving two cryptographic API calls to the HSM.
By End-User (Banking, Financial Services and Insurance (BFSI), Government, Healthcare, Manufacturing, IT and Telecommunications, Others)
End-user segmentation spans BFSI, government, healthcare, manufacturing, IT and telecommunications, and other sectors. BFSI leads adoption due to high volumes of financial transactions and strict compliance mandates. Government agencies use hardware security modules for secure communications, citizen data protection, and defense systems. Healthcare organizations secure patient records and medical devices against unauthorized access. Manufacturing and telecom sectors deploy them to protect intellectual property, control industrial processes, and secure network infrastructures. It serves as a critical enabler of security and compliance across industries where data integrity is paramount.
Segments:
Based on Type:
- LAN-Based
- PCIe-Based
- USB-Based
- Smart Cards
Based on Application:
- Payment Processing
- Code and Document Signing
- Authentication, Secure Socket Layer (SSL)
- Transport Layer Security (TLS)
- Database Encryption
Based on End-User:
- Banking
- Financial Services
- Government
- Healthcare
- Manufacturing
- IT
- Telecommunications
Based on the Geography:
- North America
- Europe
- UK
- France
- Germany
- Italy
- Spain
- Russia
- Belgium
- Netherlands
- Austria
- Sweden
- Poland
- Denmark
- Switzerland
- Rest of Europe
- Asia Pacific
- China
- Japan
- South Korea
- India
- Australia
- Thailand
- Indonesia
- Vietnam
- Malaysia
- Philippines
- Taiwan
- Rest of Asia Pacific
- Latin America
- Brazil
- Argentina
- Peru
- Chile
- Colombia
- Rest of Latin America
- Middle East
- UAE
- KSA
- Israel
- Turkey
- Iran
- Rest of Middle East
- Africa
- Egypt
- Nigeria
- Algeria
- Morocco
- Rest of Africa
Regional Analysis
North America
North America holds the largest share of the Hardware Security Modules Market at 38%, supported by advanced technology adoption, strong regulatory frameworks, and the presence of major industry players. The region’s banking, financial services, and insurance (BFSI) sector drives substantial demand through stringent compliance requirements such as PCI DSS and FIPS 140-3. Government initiatives for securing national defense, public infrastructure, and citizen data further stimulate adoption. Cloud adoption in North America has accelerated the need for hardware security modules that integrate with AWS, Microsoft Azure, and Google Cloud security services. It benefits from high investment in cybersecurity infrastructure and rapid uptake of post-quantum cryptography solutions. The U.S. dominates regional demand, followed by Canada, where regulatory compliance and critical infrastructure protection remain top priorities.
Europe
Europe accounts for 27% of the Hardware Security Modules Market, driven by strict data privacy regulations including the General Data Protection Regulation (GDPR) and eIDAS. The region’s financial institutions and payment service providers rely heavily on hardware security modules to ensure secure transactions and meet compliance obligations. Strong demand emerges from sectors such as automotive, manufacturing, and healthcare, where intellectual property protection and secure communications are vital. The market benefits from the region’s emphasis on digital sovereignty and secure digital identity initiatives. It witnesses increasing adoption in public key infrastructure (PKI) and blockchain applications to support secure document signing and transaction validation. Key growth countries include Germany, the United Kingdom, France, and the Nordics, each investing in modernizing security infrastructure across both public and private sectors.
Asia-Pacific
Asia-Pacific holds 23% of the Hardware Security Modules Market, with rapid growth fueled by expanding digital payment ecosystems, government-led cybersecurity initiatives, and increased cloud adoption. Countries such as China, Japan, South Korea, and India show strong demand for hardware security modules in banking, telecom, and government services. It benefits from rising investments in 5G networks, IoT deployments, and e-governance platforms that require secure key management and encryption capabilities. Regional manufacturers focus on producing cost-effective yet compliant solutions for domestic and export markets. The surge in mobile payments and fintech innovation in Southeast Asia further drives adoption, while cross-border data protection policies enhance market prospects. Emerging economies are increasingly integrating hardware security modules into national cybersecurity strategies to strengthen resilience against sophisticated cyberattacks.
Latin America
Latin America represents 7% of the Hardware Security Modules Market, with growing adoption in financial services, government, and energy sectors. Brazil and Mexico lead regional demand, implementing hardware security modules for secure payments, identity verification, and sensitive data protection. It gains traction through regulatory compliance efforts and the modernization of banking systems to meet global security standards. Cloud integration is expanding in the region, creating demand for hybrid solutions that combine local control with cloud scalability. Telecom operators and government agencies invest in encryption infrastructure to support digital transformation projects. Market growth remains steady as organizations address increasing cybersecurity threats and align with international compliance frameworks.
Middle East & Africa
The Middle East & Africa accounts for 5% of the Hardware Security Modules Market, with growth supported by investments in smart city projects, financial modernization, and national security initiatives. The United Arab Emirates, Saudi Arabia, and South Africa lead adoption, deploying hardware security modules for secure payment systems, defense communications, and energy sector data protection. It benefits from regional emphasis on digital governance and secure e-services. Financial institutions adopt advanced cryptographic systems to combat fraud and meet compliance standards. Expansion in cloud data centers across the Gulf region further stimulates demand for integrated hardware security solutions. Emerging African markets gradually adopt hardware security modules to secure mobile banking services and government IT infrastructures, strengthening regional growth potential.
Shape Your Report to Specific Countries or Regions & Enjoy 30% Off!
Key Player Analysis
- M-Files Corporation
- Alfresco Software, Inc.
- Oracle
- Microsoft
- DocuWare Corporation
- Hyland Software, Inc.
- Laserfiche
- International Business Machines Corporation
- Box, Inc.
- OpenText Corporation
Competitive Analysis
The Hardware Security Modules Market features include Thales Group, International Business Machines Corporation, Hewlett Packard Enterprise Development LP, Atos SE, Utimaco GmbH, Futurex, Securosys SA, Entrust Corporation, Exceet Secure Solutions GmbH, and Yubico AB. The Hardware Security Modules Market is characterized by intense competition, with vendors prioritizing innovation, compliance, and integration capabilities to secure a larger market share. Companies focus on delivering solutions with advanced cryptographic performance, low latency, and compatibility across on-premises, cloud, and hybrid environments. Emphasis on achieving global security certifications such as FIPS 140-3 and Common Criteria strengthens credibility and adoption in regulated sectors. The market sees growing investment in post-quantum cryptography readiness to address future security challenges. Providers are expanding service-based and subscription models to meet demand for flexible and cost-effective deployment options. Strategic alliances with cloud platforms, regional expansion initiatives, and R&D-driven product enhancements remain critical for addressing emerging use cases in IoT, blockchain, and 5G, ensuring sustained growth and competitive advantage.
Recent Developments
- In May 2025, Microsoft enhanced its Azure cloud platform by expanding Hardware Security Module (HSM) services within Azure Key Vault Managed HSM. This expansion focused on providing stronger cryptographic key protection, particularly for enterprise compliance needs. The enhanced offering includes FIPS 140-3 Level 3 validation for the underlying HSMs, ensuring a higher level of security for sensitive data
- In April 2025, Entrust rolled out the Entrust cryptographic security platform, which is a big step for managing keys, secrets, and certificates all in one place.
- In February 2025, Futurex became the first company in ABI Research’s payment hardware security module competitive assessment.
- In February 2025, Thales launched the OneWelcome FIDO key lifecycle management solution that enables streamlined, passwordless authentication at scale.
Market Concentration & Characteristics
The Hardware Security Modules Market demonstrates a moderately concentrated structure, with a mix of global leaders and specialized regional providers competing on technology, compliance, and integration capabilities. It is characterized by high entry barriers due to the need for advanced cryptographic expertise, significant R&D investment, and strict regulatory certification requirements. Established vendors dominate large-scale deployments in sectors such as banking, government, and cloud services, while niche players address customized or industry-specific needs. The market places strong emphasis on interoperability with multi-cloud architectures, low-latency performance, and support for emerging cryptographic standards, including post-quantum algorithms. Demand patterns are shaped by increasing regulatory enforcement, growing adoption of digital payment systems, and expansion into high-growth areas such as IoT, blockchain, and 5G security. Competitive dynamics favor companies capable of combining hardware reliability with flexible deployment models, including as-a-service offerings, to address diverse enterprise requirements.
Report Coverage
The research report offers an in-depth analysis based on Type, Application, End-User and Geography. It details leading market players, providing an overview of their business, product offerings, investments, revenue streams, and key applications. Additionally, the report includes insights into the competitive environment, SWOT analysis, current market trends, as well as the primary drivers and constraints. Furthermore, it discusses various factors that have driven market expansion in recent years. The report also explores market dynamics, regulatory scenarios, and technological advancements that are shaping the industry. It assesses the impact of external factors and global economic changes on market growth. Lastly, it provides strategic recommendations for new entrants and established companies to navigate the complexities of the market.
Future Outlook
- Demand will grow with the expansion of digital payment systems and stricter global compliance requirements.
- Adoption will increase in cloud-native and hybrid infrastructures requiring secure key management.
- Integration with post-quantum cryptography will become a core product differentiator.
- Edge computing and IoT deployments will create new opportunities for compact, ruggedized solutions.
- Service-based and subscription delivery models will gain wider acceptance across industries.
- Vendors will invest in API-enabled designs to improve interoperability with diverse IT ecosystems.
- Growth in blockchain and 5G applications will drive demand for high-throughput, low-latency encryption.
- Strategic partnerships with cloud service providers will expand market reach and integration options.
- Regulatory changes will accelerate product upgrades and certification renewals.
- Emerging markets will show faster adoption as governments strengthen national cybersecurity frameworks.




