Market Overview
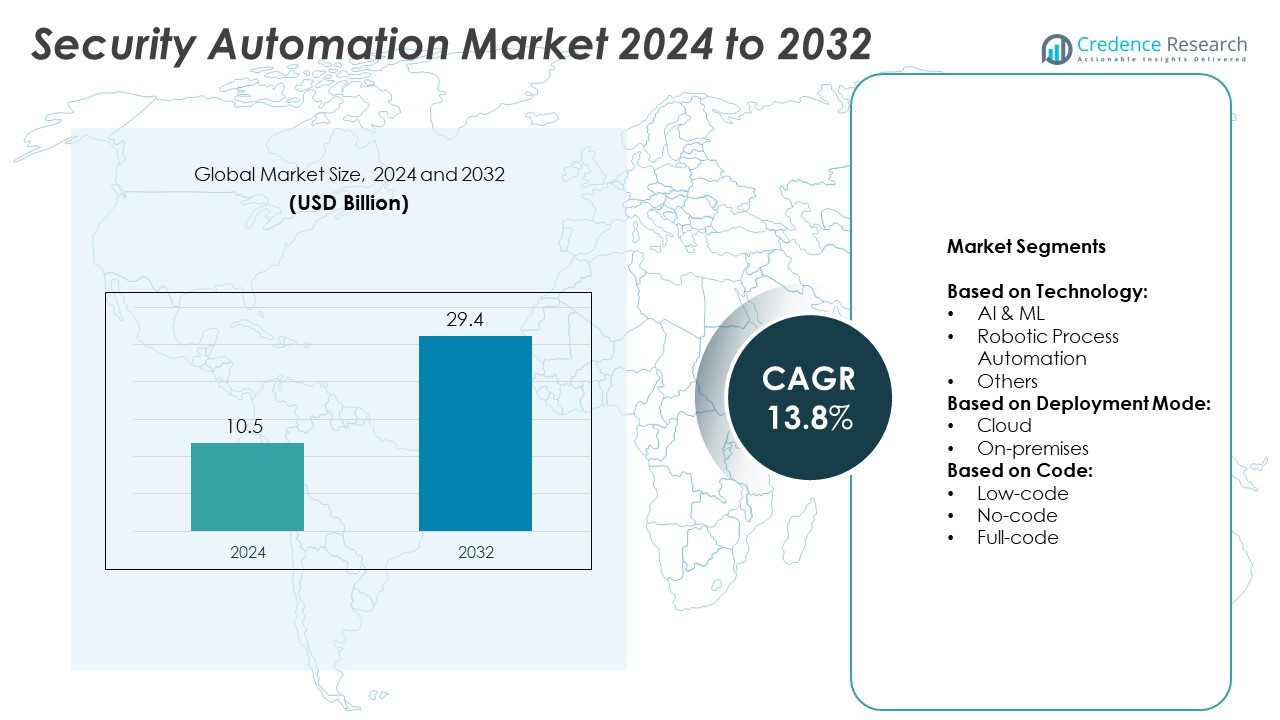
The Security Automation Market size was valued at USD 10.5 billion in 2024 and is expected to reach USD 29.4 billion by 2032, growing at a CAGR of 13.8% during the forecast period.
| REPORT ATTRIBUTE |
DETAILS |
| Historical Period |
2020-2024 |
| Base Year |
2024 |
| Forecast Period |
2025-2032 |
| Security Automation Market Size 2024 |
USD 10.5 Billion |
| Security Automation Market, CAGR |
13.8% |
| Security Automation Market Size 2032 |
USD 29.4 Billion |
The Security Automation market grows due to rising cyber threats, regulatory pressure, and digital transformation across industries. Organizations seek faster threat detection, improved incident response, and reduced manual workloads. AI, machine learning, and SOAR platforms enable real-time decision-making and efficient operations. The shift toward cloud, zero trust architecture, and DevSecOps integration further supports adoption. Enterprises prefer low-code and no-code tools to overcome skill gaps. These trends drive continuous innovation and broader deployment of automated security solutions.
North America leads the Security Automation market due to early technology adoption and strong vendor presence. Europe follows, supported by strict data regulations and rising cloud adoption. Asia-Pacific shows fast growth with increasing digitalization and cybersecurity investments in China, India, and Japan. Latin America and the Middle East are emerging markets with growing interest in cloud-based security tools. Key players driving innovation and expansion include CyberArk Software Ltd., CrowdStrike, Cisco Systems, Inc., and Palo Alto Networks.
Access crucial information at unmatched prices!
Request your sample report today & start making informed decisions powered by Credence Research Inc.!
Download Sample
Market Insights
- The Security Automation market was valued at USD 10.5 billion in 2024 and is projected to reach USD 29.4 billion by 2032, growing at a CAGR of 13.8%.
- Rising cyber threats, demand for faster response, and regulatory mandates drive the adoption of automated security solutions.
- AI, machine learning, and SOAR platforms lead market trends by enabling real-time detection, response, and orchestration.
- Enterprises prefer low-code and no-code platforms to overcome cybersecurity skill shortages and streamline operations.
- Leading companies such as CyberArk, CrowdStrike, Cisco, and Palo Alto Networks compete through innovation, cloud-native tools, and acquisitions.
- High deployment costs, integration challenges with legacy systems, and lack of skilled professionals limit adoption in small enterprises.
- North America leads the market due to early adoption, followed by Europe and Asia-Pacific, while Latin America and the Middle East show emerging demand.
Market Drivers
Growing Threat Landscape across Digital Ecosystems
The rising frequency and sophistication of cyber threats push organizations to adopt automated security solutions. Manual threat detection fails to keep pace with fast-evolving attack vectors. Security automation tools deliver real-time responses, minimizing human error. Businesses across sectors invest in proactive threat management frameworks. These platforms integrate AI, machine learning, and behavioral analytics. The Security Automation market benefits from this urgency to defend complex digital networks.
- For instance, A 2018 CrowdStrike press release actually reported that its OverWatch team stopped 25,000 attempted intrusions over the course of a year, not 250,000 daily.
Demand for Faster Incident Response and Operational Efficiency
Companies seek to reduce response time to security breaches. Automation helps streamline workflows, accelerating detection, triage, and resolution. It eliminates repetitive tasks, allowing analysts to focus on critical issues. Security Orchestration, Automation, and Response (SOAR) platforms play a key role. They enable integration of multiple tools, reducing downtime. The market reflects increasing reliance on automation for better resource optimization.
- For instance, Case studies and ROI analyses indicate that Swimlane’s platform drives significant efficiency gains for enterprises, while cost savings have been projected. A 2022 TAG Cyber report, commissioned by Swimlane, projected a 240% ROI over one year for a hypothetical large financial services company based on reasonable operating assumptions. This projected ROI was based on a financial model, not the actual performance of a real customer
Compliance Pressure and Regulatory Mandates Drive Automation
Strict global regulations around data privacy and breach notification support market growth. Organizations must ensure rapid incident handling to avoid fines and reputational damage. Automation tools help maintain audit trails, ensure policy enforcement, and support compliance reporting. Sectors like finance, healthcare, and retail adopt automation to meet regional and international standards. It enables consistent enforcement of security policies across infrastructure. The Security Automation market responds to growing compliance challenges with scalable tools.
Rapid Adoption of Cloud, IoT, and Hybrid IT Environments
Enterprises are shifting to hybrid architectures that increase security complexity. Cloud-native workloads and IoT ecosystems generate vast data, creating blind spots. Automation solutions enhance visibility across cloud and on-premise environments. They adapt to diverse infrastructures and ensure continuous monitoring. It supports businesses in securing multi-cloud strategies without expanding headcount. The market benefits from growing demand to secure distributed digital assets.
Market Trends
Integration of Artificial Intelligence for Advanced Threat Detection
AI continues to reshape security operations by offering real-time threat detection and predictive analytics. Machine learning models process large data sets to identify unusual behavior across networks. These models improve over time, reducing false positives and alert fatigue. Vendors integrate AI engines into platforms for autonomous decision-making. Businesses adopt AI-driven tools to strengthen detection accuracy and speed. The Security Automation market reflects this shift toward intelligent threat identification.
- For instance, the Cisco Talos threat intelligence team reported in its 2024 Year in Review that its threat telemetry is powered by data from over 46 million global devices across 193 countries and regions, and that it processes more than 886 billion security events per day
Adoption of SOAR Platforms Across Enterprises
Security Orchestration, Automation, and Response (SOAR) platforms are gaining traction among large and mid-sized enterprises. These tools unify various security solutions into a centralized system. SOAR platforms help automate playbooks, standardize incident response, and improve collaboration. Companies reduce mean time to respond (MTTR) and enhance overall security posture. The trend supports adoption in sectors with complex IT infrastructures. The Security Automation market benefits from increasing demand for end-to-end orchestration.
- For instance, Security automation typically reduces the number of incidents that security analysts must manually investigate. Some organizations have reported substantial efficiency gains, with one user noting a reduction in the volume of incidents requiring manual review by 75%, from approximately 1,000 to 250 incidents per day
Shift Toward Zero Trust Security Architecture
Zero Trust principles are influencing automation strategies across industries. Organizations no longer rely on perimeter-based security models. They implement identity-centric policies that demand verification at every access point. Automation tools enforce these policies in real time and adapt to user behavior. This model reduces lateral movement and insider threat risks. It supports market growth by aligning with modern enterprise architectures.
Growth in Cloud-Native Security Solutions
Cloud adoption continues to accelerate across industries, driving need for scalable, cloud-native security automation. These solutions enable policy enforcement and threat monitoring in dynamic environments. Vendors offer APIs and integration support for platforms like AWS, Azure, and Google Cloud. Businesses prioritize tools that operate seamlessly within DevSecOps pipelines. Cloud-native automation improves security coverage without disrupting workflows. The Security Automation market reflects this shift to support agile, digital-first operations.
Market Challenges Analysis
High Implementation Costs and Integration Complexity
Security automation tools require significant upfront investment in software, infrastructure, and skilled resources. Small and medium enterprises often struggle to allocate budget for advanced platforms. Integrating automation with legacy systems adds technical complexity and delays adoption. Customization needs vary by organization, increasing deployment time and cost. Without proper planning, automation efforts may disrupt existing workflows. The Security Automation market faces resistance from companies concerned about return on investment and operational risk.
Lack of Skilled Professionals and Awareness Gaps
Organizations face a shortage of skilled cybersecurity professionals who can manage and optimize automated systems. Automation tools demand expertise in scripting, system orchestration, and data analysis. Many security teams lack training to fully leverage platform capabilities. Limited awareness about solution benefits also slows decision-making across industries. Without the right personnel, companies fail to realize efficiency gains or mitigate threats effectively. It restricts market growth and slows broader industry adoption.
Market Opportunities
Rising Demand from Emerging Economies and SME Sector
Developing regions such as Asia-Pacific, Latin America, and the Middle East are witnessing increased digital adoption. Businesses in these areas expand IT operations, creating demand for scalable and affordable security solutions. SMEs seek automated tools to compensate for limited in-house security teams. Vendors can offer cloud-based, modular platforms tailored for cost-sensitive markets. Governments also invest in cybersecurity infrastructure, further supporting adoption. The Security Automation market has untapped growth potential in these regions.
Expansion of AI and IoT Security Use Cases
The proliferation of IoT devices and connected systems introduces new security risks across industries. Automation can address these risks by delivering continuous monitoring and response at scale. AI-based systems improve threat detection accuracy in real-time environments. Sectors like healthcare, manufacturing, and transportation demand automated solutions to secure distributed networks. Vendors offering specialized use case solutions can expand into vertical-specific markets. It opens new avenues for innovation and revenue generation.
Market Segmentation Analysis:
By Technology:
AI and ML hold the largest share due to their ability to detect patterns and threats in real time. These tools support anomaly detection, predictive analytics, and faster response decisions. Robotic Process Automation (RPA) simplifies routine tasks such as log analysis, user provisioning, and alert triage. It reduces workload for security teams and ensures consistent execution. The “Others” category includes rule-based systems and basic scripting, often used by smaller enterprises. The Security Automation market benefits from rising integration of AI for autonomous threat handling.
- For instance, Tufin helped a multinational bank eliminate a 12-month security policy review backlog by automating continuous compliance for more than 4,000 firewall rules previously managed in spreadsheets.
By Deployment Mode:
Cloud-based solutions lead due to flexibility, scalability, and faster deployment. Enterprises prefer cloud platforms to monitor distributed IT assets and remote endpoints. Cloud models also ease integration with third-party APIs and SIEM platforms. On-premises deployment remains in demand among sectors with strict data control and regulatory requirements. These include defense, finance, and government agencies that require complete data residency. It supports customers who prioritize local storage and internal infrastructure management.
- For instance, a 2022 report by (ISC)² revealed a global shortfall of 3.4 million cybersecurity professionals, a factor that directly impacts security and automation efforts.
By Code:
Low-code platforms gain popularity for enabling faster deployment without deep technical skills. Security teams use drag-and-drop workflows to automate tasks and reduce time to value. No-code platforms target non-technical users who manage basic processes without writing scripts. These tools help bridge skill gaps in understaffed security teams. Full-code platforms remain essential for large enterprises with complex environments. It supports deep customization, fine-grained controls, and high-performance automation use cases. The Security Automation market grows across all code types as vendors cater to varying skill levels and use case demands.
Segments:
Based on Technology:
- AI & ML
- Robotic Process Automation
- Others
Based on Deployment Mode:
Based on Code:
- Low-code
- No-code
- Full-code
Based on the Geography:
- North America
- Europe
- UK
- France
- Germany
- Italy
- Spain
- Russia
- Belgium
- Netherlands
- Austria
- Sweden
- Poland
- Denmark
- Switzerland
- Rest of Europe
- Asia Pacific
- China
- Japan
- South Korea
- India
- Australia
- Thailand
- Indonesia
- Vietnam
- Malaysia
- Philippines
- Taiwan
- Rest of Asia Pacific
- Latin America
- Brazil
- Argentina
- Peru
- Chile
- Colombia
- Rest of Latin America
- Middle East
- UAE
- KSA
- Israel
- Turkey
- Iran
- Rest of Middle East
- Africa
- Egypt
- Nigeria
- Algeria
- Morocco
- Rest of Africa
Regional Analysis
North America
North America holds the largest share in the Security Automation market, accounting for 36.2% of the global revenue in 2024. This region benefits from early adoption of advanced cybersecurity technologies and strong presence of global vendors. The U.S. leads in enterprise spending on AI-driven security systems, driven by frequent high-impact cyber incidents and growing regulatory pressure. Companies across financial services, healthcare, and critical infrastructure deploy security automation to reduce response time and comply with frameworks like NIST and HIPAA. SOAR platforms and cloud-native security tools have high uptake among large enterprises and government agencies. Canada also invests in digital transformation, particularly within its public and energy sectors, boosting demand for automated threat detection and compliance solutions. With growing adoption of zero trust models and integration of AI in incident response systems, North America continues to anchor global advancements in this market.
Europe
Europe captures 27.4% of the Security Automation market share in 2024, making it the second-largest region globally. The European Union’s strict data privacy regulations, including GDPR, drive demand for automated solutions to support compliance, breach detection, and audit readiness. Countries like Germany, the UK, and France see rising deployment of AI-enhanced security tools within manufacturing, finance, and government sectors. Enterprises in these nations use automation to align with growing cyber insurance requirements and to avoid penalties from regulatory breaches. Demand for low-code and no-code automation platforms rises due to workforce shortages in cybersecurity roles. European vendors also strengthen the market by focusing on privacy-by-design solutions and offering region-specific compliance features. The region’s growing focus on sovereign cloud and cross-border data management reinforces the adoption of cloud-based security automation.
Asia-Pacific
Asia-Pacific accounts for 22.1% of the global market share and shows the fastest growth trajectory. The region’s rapid digital transformation, especially in China, India, Japan, and South Korea, increases exposure to cyber risks. Enterprises across manufacturing, telecom, and BFSI sectors adopt automation to manage threats in real-time and protect large volumes of user data. Government-led programs like India’s Digital India and China’s Cybersecurity Law encourage investments in cybersecurity frameworks and automation. Local vendors collaborate with global firms to offer AI- and ML-powered solutions tailored to regional needs. Cloud-based deployments dominate, driven by expanding SME adoption and flexible pricing models. Asia-Pacific continues to gain ground due to strong IT services sectors and increasing cybersecurity awareness.
Latin America
Latin America holds 7.3% of the Security Automation market share in 2024, supported by digital growth and rising cloud adoption. Brazil and Mexico are the primary contributors, where banking, telecom, and retail industries lead automation investments. Organizations in these countries use automated systems to respond to ransomware attacks and manage compliance under evolving local laws. Awareness of cybersecurity risk is growing, but budget constraints and skills shortages still limit adoption. Cloud-first strategies help overcome some infrastructure gaps, especially among SMEs. The region sees a steady rise in interest for low-code security automation that offers ease of deployment and cost efficiency.
Middle East and Africa
The Middle East and Africa region contributes 7.0% to the global market share. Countries like the UAE, Saudi Arabia, and South Africa drive growth through national cybersecurity strategies and digital economy programs. Enterprises across oil and gas, defense, and government invest in automation to secure critical infrastructure and meet regional compliance mandates. Large-scale events and smart city initiatives increase the need for real-time threat response and centralized security control. While infrastructure gaps persist in parts of Africa, local governments and international vendors collaborate on pilot projects to improve cybersecurity maturity. The market benefits from gradual cloud adoption and increased focus on training programs to close the skills gap. As cybersecurity threats become more sophisticated, the demand for AI-based and orchestration-driven security automation tools grows steadily.
Shape Your Report to Specific Countries or Regions & Enjoy 30% Off!
Key Player Analysis
- Red Hat, Inc.
- CrowdStrike
- Swimlane Inc.
- Cisco Systems, Inc.
- Tufin
- IBM Corporation
- CyberArk Software Ltd.
- Splunk Inc.
- Secureworks, Inc.
- Palo Alto Networks
Competitive Analysis
The leading players in the Security Automation market include CyberArk Software Ltd., CrowdStrike, Cisco Systems, Inc., Palo Alto Networks, IBM Corporation, Red Hat, Inc., Secureworks, Inc., Splunk Inc., Swimlane Inc., and Tufin.These companies focus on delivering advanced threat detection, orchestration, and response capabilities. They compete by offering integrated platforms that support AI-driven decision-making and real-time security operations. Vendors enhance product portfolios through cloud-native features, low-code workflows, and API-based integration. The market sees increased investment in Security Orchestration, Automation, and Response (SOAR) platforms, where vendors differentiate through scalability, threat intelligence, and ecosystem compatibility. Strategic acquisitions and partnerships also play a key role in expanding service offerings and geographic presence. Enterprises prefer vendors with proven reliability, broad tool integration, and support for complex IT environments. Product innovation, ease of deployment, and regulatory compliance remain critical factors in gaining market share. Key players invest in customer education and managed services to support adoption across varied user bases. The competitive landscape reflects a balance between global technology giants and specialized security automation providers.
Recent Developments
- In August 2025, CrowdStrike earned recognition as a Leader in the IDC MarketScape for Worldwide Incident Response Services.
- In July 2025, CyberArk launched tools to secure AI agents—Secure Cloud Access (SCA) MCP Server and Agent Guard—on AWS Marketplace.
- In July 2025, Palo Alto Networks made a strategic play to enter identity security via a pending acquisition of CyberArk.
Report Coverage
The research report offers an in-depth analysis based on Technology, Deployment Mode, Code and Geography. It details leading market players, providing an overview of their business, product offerings, investments, revenue streams, and key applications. Additionally, the report includes insights into the competitive environment, SWOT analysis, current market trends, as well as the primary drivers and constraints. Furthermore, it discusses various factors that have driven market expansion in recent years. The report also explores market dynamics, regulatory scenarios, and technological advancements that are shaping the industry. It assesses the impact of external factors and global economic changes on market growth. Lastly, it provides strategic recommendations for new entrants and established companies to navigate the complexities of the market.
Future Outlook
- AI and machine learning will drive faster, more accurate threat detection across all sectors.
- SOAR platforms will become essential for centralized security response and operational efficiency.
- Cloud-native security automation tools will dominate deployments in hybrid and multi-cloud environments.
- Zero trust models will expand, requiring automation to enforce identity-based access policies.
- Low-code and no-code platforms will grow to address the global cybersecurity skills shortage.
- Integration with DevSecOps pipelines will support continuous security in agile development cycles.
- Demand for real-time data visibility and analytics will increase across IoT and OT networks.
- Small and mid-sized enterprises will adopt flexible, modular security automation solutions.
- Regulatory compliance needs will push more organizations to automate auditing and reporting.
- Regional partnerships and government cybersecurity programs will encourage faster market adoption.




