Market Overview
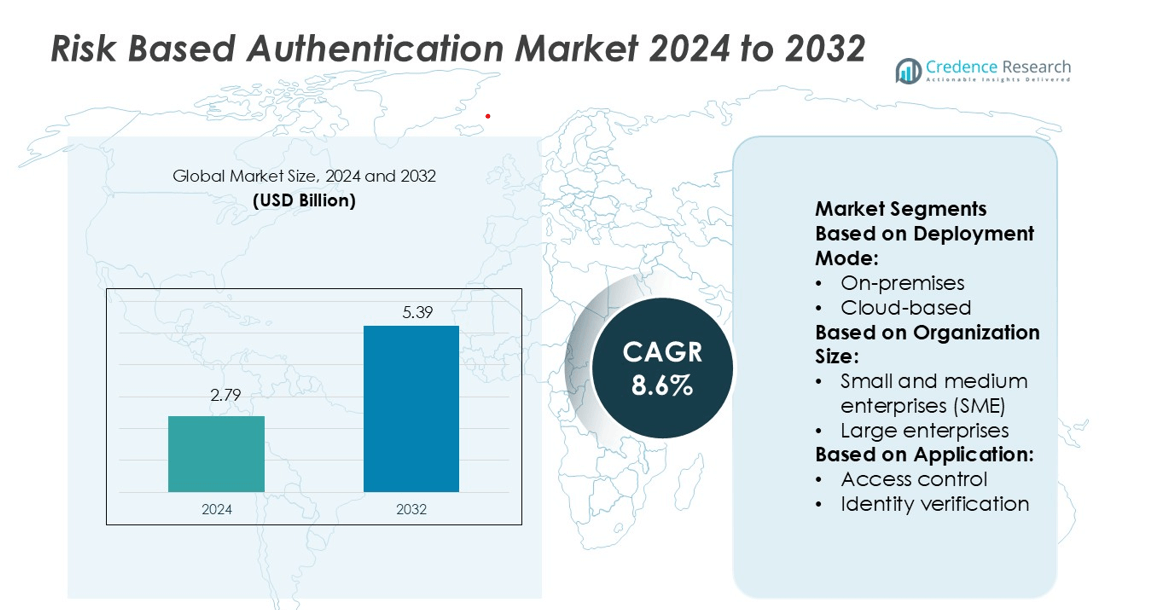
Risk Based Authentication Market size was valued USD 2.79 billion in 2024 and is anticipated to reach USD 5.39 billion by 2032, at a CAGR of 8.6% during the forecast period.
| REPORT ATTRIBUTE |
DETAILS |
| Historical Period |
2020-2023 |
| Base Year |
2024 |
| Forecast Period |
2025-2032 |
| Risk Based Authentication Market Size 2024 |
USD 2.79 billion |
| Risk Based Authentication Market, CAGR |
8.6% |
| Risk Based Authentication Market Size 2032 |
USD 5.39 billion |
The Risk Based Authentication Market is led by strong competition among established vendors focused on adaptive security innovation. North America leads the global market with a 36% share, supported by advanced cybersecurity infrastructure, strict compliance regulations, and early adoption of digital technologies. The region’s dominance is reinforced by high enterprise spending on cloud security and Zero Trust frameworks. Companies are prioritizing AI-based authentication, real-time risk scoring, and seamless user verification to reduce fraud and enhance protection. This regional leadership, combined with continuous product advancements, is setting the global standard for next-generation authentication practices.
Market Insights
- The Risk Based Authentication Market was valued at USD 2.79 billion in 2024 and is projected to reach USD 5.39 billion by 2032, growing at a CAGR of 8.6%.
- Rising cyber threats, regulatory pressure, and growing cloud adoption are driving demand for adaptive authentication solutions across multiple industries.
- AI-driven authentication, Zero Trust integration, and biometric technologies are key trends shaping product development and market expansion.
- The market is highly competitive, with vendors focusing on real-time risk scoring and frictionless security experiences to strengthen their positions.
- North America leads the global market with a 36% share, followed by Europe with 28% and Asia Pacific with 22%, while the cloud deployment segment holds the dominant share due to its scalability and enterprise adoption.
Access crucial information at unmatched prices!
Request your sample report today & start making informed decisions powered by Credence Research Inc.!
Download Sample
Market Segmentation Analysis:
By Deployment Mode
Cloud-based deployment dominates the Risk Based Authentication Market with a 63% share in 2024. Organizations favor cloud-based solutions due to their scalability, lower upfront investment, and faster integration with existing IT systems. The segment benefits from growing demand for remote access security and real-time risk analysis. Continuous updates and advanced AI-driven threat detection further enhance adoption. In contrast, on-premises deployment remains relevant for sectors with strict data residency rules, but its share continues to decline as enterprises shift to cloud-native platforms for improved agility and cost efficiency.
- For instance, WebAIM’s 2023–2024 Screen Reader User Survey collected responses from 1,539 participants and found that approximately 40.5% cited JAWS as their primary desktop or laptop screen reader, while 37.7% selected NVDA.
By Organization Size
Large enterprises hold a 59% share of the Risk Based Authentication Market in 2024. These companies handle high transaction volumes and complex user access environments, driving the need for advanced, layered security frameworks. Adoption is supported by larger budgets, regulatory compliance needs, and a strong focus on protecting sensitive data. Enterprises in banking, healthcare, and government sectors lead the demand. Small and medium enterprises are steadily increasing adoption due to affordable cloud-based options, but large enterprises continue to dominate due to their extensive security infrastructure investments.
- For instance, Apple had sold more than 3 billion iPhones, all equipped with built-in VoiceOver screen reader capability, significantly broadening access to mobile accessibility tools across general and assistive user populations worldwide.
By Application
Fraud prevention leads the application segment with a 41% market share in 2024. Rising digital transactions, increasing account takeover incidents, and stricter compliance rules drive adoption in this sub-segment. Financial institutions and e-commerce platforms deploy risk-based authentication to detect suspicious behavior in real time. Identity verification and transaction security follow closely, supported by the need for secure customer onboarding and multi-factor authentication. Regulatory pressure also boosts the compliance management sub-segment. As cyber threats evolve, fraud prevention remains the primary driver for implementing adaptive authentication solutions.
Key Growth Drivers
Rising Cybersecurity Threats
The growing frequency of cyberattacks is driving strong demand for advanced authentication methods. Risk-based authentication enables organizations to assess threats in real time and adjust security levels dynamically. This approach minimizes unauthorized access while ensuring a smooth user experience. Industries such as banking, healthcare, and e-commerce are adopting the technology to secure sensitive data. The rising number of phishing, credential theft, and account takeover incidents is pushing enterprises to invest in adaptive authentication systems, fueling consistent market expansion.
- For instance, WebAIM’s 2024 Screen Reader User Survey, which gathered responses from over 1,500 users, revealed that 37.3% of participants commonly use Narrator—Microsoft’s integrated screen reader for Windows desktop.
Rapid Digital Transformation
The shift toward digital services across industries is increasing the need for secure user authentication. Risk-based authentication supports secure transactions and access management across cloud platforms, mobile apps, and remote work systems. Organizations are integrating these solutions to maintain compliance and protect digital assets. Digital transformation in sectors such as retail, BFSI, and government is boosting deployments. Strong regulatory pressure for data protection is also encouraging investment in adaptive security tools, positioning risk-based authentication as a core security component.
- For instance, Ghotit introduced its Analytics feature in Version 10, which allows users to track their writing activity. In early use, users checked around 750 words, a figure that quickly rose to 4,000 words in a short time—demonstrating the tool’s role in enabling expanding writing efforts among users with dyslexia or dysgraphia.
Growing Regulatory Compliance Requirements
Regulations like GDPR, PSD2, and CCPA are compelling organizations to adopt strong authentication measures. Risk-based authentication helps businesses meet compliance requirements by continuously assessing risk levels without creating friction for legitimate users. Enterprises are using these solutions to ensure data integrity, protect user privacy, and avoid penalties. This compliance-driven demand is particularly strong in finance, healthcare, and government sectors. As regulatory frameworks expand globally, companies are prioritizing advanced authentication tools, creating a solid growth pathway for the market.
Key Trends & Opportunities
Expansion of AI and Machine Learning
AI and machine learning are transforming how risk-based authentication systems assess user behavior. These technologies enable faster anomaly detection and more precise risk scoring. Companies are leveraging predictive analytics to identify threats in real time without compromising user experience. As AI models become more accurate, authentication systems can adapt dynamically to various risk levels. This shift creates opportunities for vendors to offer intelligent and automated security solutions, improving both protection and operational efficiency.
- For instance, the Android Accessibility Suite—including TalkBack—has been downloaded more than 5 billion times worldwide according to the Google Play Store, highlighting how deeply integrated and widely deployed cloud-enabled accessibility tools have become in everyday mobile ecosystems.
Integration with Zero Trust Security Models
The increasing adoption of Zero Trust frameworks is accelerating risk-based authentication deployments. These solutions align well with continuous verification principles, ensuring access is granted only after risk evaluation. Organizations are integrating adaptive authentication into Zero Trust architectures to secure cloud workloads, endpoints, and remote access. This integration enhances visibility and control while minimizing breaches. Vendors offering seamless Zero Trust integration are gaining strong market traction, especially in highly regulated sectors like banking and defense.
- For instance, ViewPlus Technologies has delivered over 10,000 embossers worldwide, empowering blind and low-vision learners with tactile graphics and braille access across educational and personal use contexts.
Growth of Cloud and Remote Work Ecosystems
The rise in remote work and cloud-based services is creating new opportunities for risk-based authentication providers. Enterprises need flexible, scalable solutions that secure user access across multiple platforms. Adaptive authentication allows frictionless login for low-risk users while applying stronger measures when needed. This helps balance security with usability. The expanding hybrid work model is pushing companies to invest in these solutions to protect distributed networks, boosting demand in both large enterprises and SMEs.
Key Challenges
High Implementation Costs
Adopting risk-based authentication requires significant investment in infrastructure, integration, and training. Smaller enterprises often face budget constraints that limit large-scale deployment. The complexity of integrating authentication systems with existing IT architecture increases costs further. Many organizations also need to upgrade their identity management frameworks to support adaptive security. These financial and operational barriers can slow market penetration, particularly in developing regions with limited cybersecurity budgets.
Concerns Over Data Privacy and User Experience
Risk-based authentication systems rely on analyzing user behavior and contextual data, raising privacy concerns. Strict data protection regulations require companies to handle such data with care. Poorly implemented systems can also lead to false positives, causing friction for legitimate users. Balancing strong security with a seamless user experience remains challenging for many organizations. These privacy and usability concerns can reduce adoption rates, especially among businesses prioritizing customer satisfaction.
Regional Analysis
North America
North America dominates the Risk Based Authentication Market with a 36% share. The region benefits from strong regulatory frameworks, high digital adoption, and a mature cybersecurity ecosystem. Industries such as BFSI, healthcare, and retail are leading in deploying adaptive authentication to protect sensitive data. High rates of cloud adoption and remote work models increase the need for advanced security solutions. The presence of major technology vendors and significant investments in AI-based security tools further boost market growth. The U.S. remains the largest contributor, supported by strict compliance requirements and rapid technological innovation.
Europe
Europe accounts for 28% of the market share, driven by robust data protection regulations such as GDPR and PSD2. These laws encourage enterprises to adopt adaptive security frameworks to ensure compliance and safeguard user privacy. BFSI, government, and telecom sectors are major adopters of risk-based authentication solutions. The region is also seeing increased investment in Zero Trust architectures, further accelerating adoption. Countries like Germany, the U.K., and France lead in deployment, supported by strong regulatory enforcement and advanced IT infrastructure. Rising cross-border transactions and identity fraud concerns are key growth drivers.
Asia Pacific
Asia Pacific holds a 22% market share and is experiencing the fastest growth rate globally. The rapid expansion of digital banking, e-commerce, and cloud-based applications is driving demand for adaptive authentication solutions. Governments are implementing cybersecurity regulations and digital identity initiatives to enhance security frameworks. Major economies like China, India, Japan, and South Korea are investing in AI and behavioral analytics to strengthen threat detection. Increasing cybercrime incidents and a growing SME base are fueling large-scale adoption. This dynamic environment positions the region as a critical growth engine for the global market.
Latin America
Latin America captures a 7% market share and shows steady adoption of risk-based authentication solutions. Financial institutions and government agencies are early adopters, driven by rising cyberattacks and digital payment usage. Brazil and Mexico are leading the regional market with increased investment in security infrastructure. Regulatory developments around data privacy are pushing enterprises to adopt adaptive authentication methods. Although the market is less mature compared to North America and Europe, increasing mobile penetration and fintech expansion present significant growth opportunities for technology providers.
Middle East & Africa
The Middle East & Africa region holds a 7% market share, with demand rising steadily. Governments and financial institutions are implementing advanced authentication systems to counter increasing cyber threats. Gulf countries such as the UAE and Saudi Arabia are leading with strong regulatory frameworks and smart city projects. Growing investments in digital transformation and cloud services are driving adoption across multiple sectors. The region still faces challenges related to infrastructure gaps, but increasing public-private partnerships and regulatory support are creating favorable conditions for market growth.
Market Segmentations:
By Deployment Mode:
By Organization Size:
- Small and medium enterprises (SME)
- Large enterprises
By Application:
- Access control
- Identity verification
By Geography
- North America
- Europe
- Germany
- France
- U.K.
- Italy
- Spain
- Rest of Europe
- Asia Pacific
- China
- Japan
- India
- South Korea
- South-east Asia
- Rest of Asia Pacific
- Latin America
- Brazil
- Argentina
- Rest of Latin America
- Middle East & Africa
- GCC Countries
- South Africa
- Rest of the Middle East and Africa
Competitive Landscape
The Risk Based Authentication Market features strong competition from key players including IBM, Micro Focus, CA Technologies, Crossmatch, RSA Security, EZMCOM, ForgeRock, SecureAuth, OneSpan, and Gemalto. The Risk Based Authentication Market is characterized by intense competition and rapid technological advancements. Vendors are focusing on integrating AI, behavioral analytics, and machine learning to deliver more accurate and adaptive security solutions. The growing adoption of Zero Trust architectures and cloud-based platforms is shaping product development strategies. Companies are investing in advanced risk scoring mechanisms to detect anomalies in real time and strengthen access control. Strategic collaborations, product innovations, and compliance with global data protection regulations are key factors driving market differentiation. This competitive environment is accelerating innovation, improving user experience, and enhancing overall security standards.
Shape Your Report to Specific Countries or Regions & Enjoy 30% Off!
Key Player Analysis
- Crossmatch
- OneSpan
- ForgeRock
- CA Technologies
- RSA Security
- IBM
- Gemalto
- EZMCOM
- SecureAuth
- Micro Focus
Recent Developments
- In March 2025, Hawcx Inc., one of the prominent players in intelligent passwordless authentication, reached a major milestone with the launch of its advanced platform. This innovative solution aims to transform authentication for enterprises and end-users by offering a perfect balance of security and convenience, marking the beginning of a new era in digital authentication.
- In June 2024, REA launched a fully passwordless sign-in experience across its major brands, marking a significant step in improving user security and data protection.
- In April 2024, Center Identity, a prominent cybersecurity firm, introduced its patented secret location authentication technology, revolutionizing how businesses handle digital identity for their workforce. This innovative approach allows users to verify their identity by selecting a secret location on a map.
- In March 2024, KSI Keyboards and AuthX partnered to enhance passwordless security in healthcare settings. Announced just ahead of the HIMSS24 conference in Orlando, this collaboration combines KSI’s advanced keyboards featuring integrated RFID and fingerprint biometrics with AuthX’s single sign-on (SSO) platform
Report Coverage
The research report offers an in-depth analysis based on Deployment Mode, Organization Size, Application and Geography. It details leading market players, providing an overview of their business, product offerings, investments, revenue streams, and key applications. Additionally, the report includes insights into the competitive environment, SWOT analysis, current market trends, as well as the primary drivers and constraints. Furthermore, it discusses various factors that have driven market expansion in recent years. The report also explores market dynamics, regulatory scenarios, and technological advancements that are shaping the industry. It assesses the impact of external factors and global economic changes on market growth. Lastly, it provides strategic recommendations for new entrants and established companies to navigate the complexities of the market.
Future Outlook
- The adoption of AI and machine learning will enhance threat detection accuracy.
- Zero Trust security frameworks will drive wider deployment across industries.
- Cloud-based authentication platforms will dominate new solution rollouts.
- Integration with biometric and behavioral analytics will improve security layers.
- Regulatory pressure will continue to boost investment in adaptive authentication.
- SMEs will adopt cost-efficient risk-based solutions at a faster pace.
- Real-time risk scoring models will become standard in enterprise security strategies.
- Partnerships between vendors and enterprises will strengthen global market presence.
- Advanced authentication solutions will reduce fraud and enhance user trust.
- Continuous innovation will shape a more intelligent and seamless authentication ecosystem.




